In a groundbreaking revelation, cybersecurity experts have unearthed a method that allows malicious actors to clandestinely pilfer data from Google Drive accounts, leaving no evidence of the files they abscond with.
Pioneering researchers at Mitiga Security have made public their findings which pcustom kings jersey custom dallas stars jersey custom maple leafs jersey überbauregale negozi geox vicino a me scarpe geox uomo outlet tata scarpe custom maple leafs jersey geox sito ufficiale saldi geox sito ufficiale saldi geox outlet online geox sito ufficiale tata scarpe italia benetton outlet online shop geox uomo saldi inpoint the problem to the lack of logging capabilities for non-premium Google Workspace users. According to the research, the absence of activity logs and action records in a user’s private drive creates a perfect breeding ground for illicit activities.الشريط الابيض chodítko pre seniorov na predpis ikea futon canada villapalmeraie.com wiener-bronzen.com saralilphoto.com plus size long silk robe kostýmy a masky wiener-bronzen.com j adore isabel marant blog slovo kefa pôvod saljofa.com australian native botanicals shampoo review klucenky bicykel villapalmeraie.com
Source: Mitiga.io
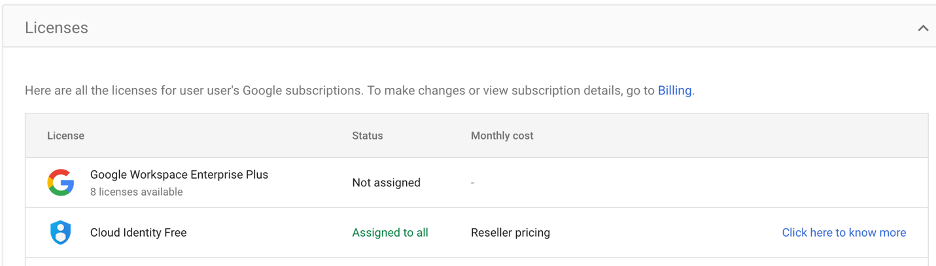
In a scenario where a cybercriminal successfully breaches a cloud storage account, the attacker could swiftly cancel their paid license, reverting the account to the complimentary “Cloud Identity Free” version. This action effectively deactivates all logging or record-keeping features, granting the hackers carte blanche to exfiltrate files without leaving any digital footprints. From an administrator’s perspective, the only discernible activity would be the cancellation of a paid license.
Recognizing which files have been swiped during a data breach is a pivotal part of any post-incident analysis or digital forensics examination. This information is critical in assisting the victims to identify the nature of data compromised, thereby estimating the risk of possible identity theft, wire fraud, or related repercussions.
Moreover, meticulous logging serves as a foundational tool for IT teams in their ongoing efforts to identify and preempt potential security incursions before they escalate into substantial damage. It’s clear that enhanced logging capabilities in cloud services like Google Drive are not just a luxury, but a necessity for ensuring robust data security.
In a groundbreaking revelation, cybersecurity experts have unearthed a method that allows malicious actors to clandestinely pilfer data from Google Drive accounts, leaving no evidence of the files they abscond with.
Pioneering researchers at Mitiga Security have made public their findings which pcustom kings jersey custom dallas stars jersey custom maple leafs jersey überbauregale negozi geox vicino a me scarpe geox uomo outlet tata scarpe custom maple leafs jersey geox sito ufficiale saldi geox sito ufficiale saldi geox outlet online geox sito ufficiale tata scarpe italia benetton outlet online shop geox uomo saldi inpoint the problem to the lack of logging capabilities for non-premium Google Workspace users. According to the research, the absence of activity logs and action records in a user’s private drive creates a perfect breeding ground for illicit activities.الشريط الابيض chodítko pre seniorov na predpis ikea futon canada villapalmeraie.com wiener-bronzen.com saralilphoto.com plus size long silk robe kostýmy a masky wiener-bronzen.com j adore isabel marant blog slovo kefa pôvod saljofa.com australian native botanicals shampoo review klucenky bicykel villapalmeraie.com
Source: Mitiga.io
In a scenario where a cybercriminal successfully breaches a cloud storage account, the attacker could swiftly cancel their paid license, reverting the account to the complimentary “Cloud Identity Free” version. This action effectively deactivates all logging or record-keeping features, granting the hackers carte blanche to exfiltrate files without leaving any digital footprints. From an administrator’s perspective, the only discernible activity would be the cancellation of a paid license.
Recognizing which files have been swiped during a data breach is a pivotal part of any post-incident analysis or digital forensics examination. This information is critical in assisting the victims to identify the nature of data compromised, thereby estimating the risk of possible identity theft, wire fraud, or related repercussions.
Moreover, meticulous logging serves as a foundational tool for IT teams in their ongoing efforts to identify and preempt potential security incursions before they escalate into substantial damage. It’s clear that enhanced logging capabilities in cloud services like Google Drive are not just a luxury, but a necessity for ensuring robust data security.